PseudonymizationㆍCombination of Pseudonymized Information
Overview
What is pseudonymized information?
Information that makes it impossible to identify a particular individual without the use or combination of additional information for restoring the information to its original state by pseudonymizing personal information
Legal basis
- Paragraph 2 of Article 28-1 of the Personal Information Protection Act (Definitions)
- Paragraph 2 of Article 28-2 of the Personal Information Protection Act (Processing of Pseudonymous Data)
Necessity of pseudonymization
As personal information contains any information about an individual, various problems may occur, such as violation of privacy in the process of processing/using the personal information. To safely use personal information, technical safety measures (pseudonymization) are taken to prevent information about a particular individual from being exposed.
Purposes and targets of pseudonymization
-

- Statistics
- Quantitative information about a particular group or target
-

- Scientific research
- Research that applies scientific methods, e.g. development and demonstration of technologies, fundamental research, applied research and privately-funded research
-

- Archive in the public interest
- Preserving records and information that need to be continuously accessed for public interests
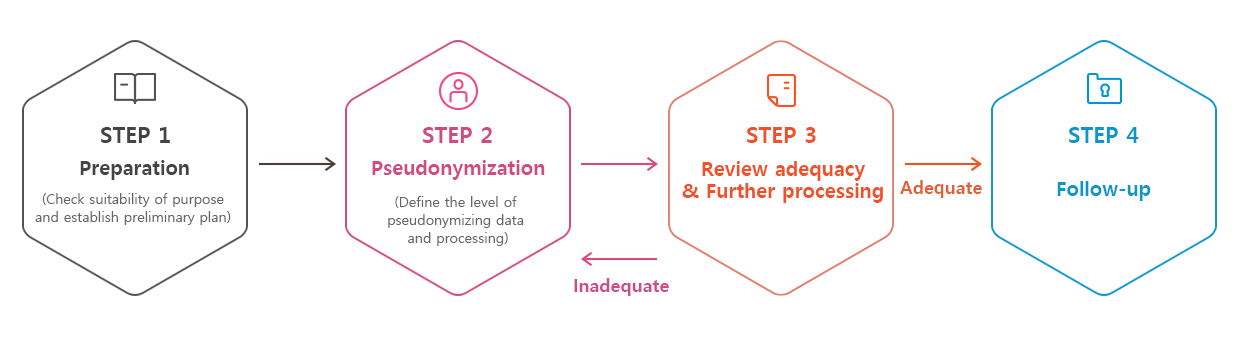
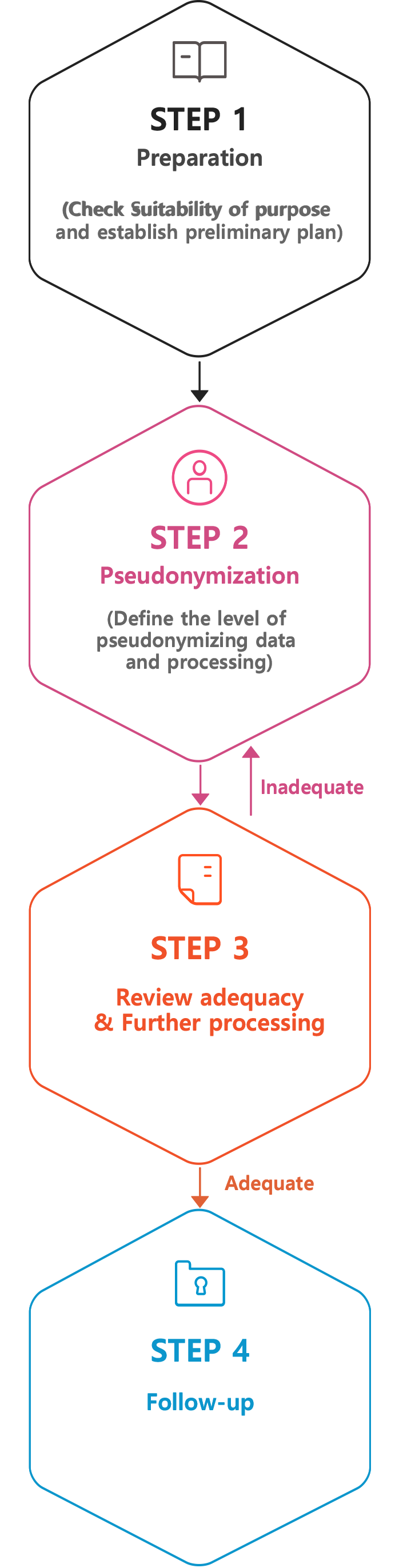
Pseudonymization Process
-
- STEP 1
- Preparation
- (Suitability for purpose and preliminary plan)
-
- STEP 2
- Pseudonymization
- (Defining the level of pseudonymizing information and processing)
-
- STEP 3
- Adequacy Review & Additional Processing
- Preserving records worth accessing continuously for the benefit of the public
- Adeguate
- Follow-up
- Inadeguate
- (Defining the level of pseudonymizing information and processing)
1. Preparation
Set up a preliminary plan including specific purposes to define the subjects and the level of pseudonymization.
2. Pseudonymization
In the process of pseudonymization, too, the principle of minimum use and collection of personal information should be maintained. In order to decide the method of pseudonymization, processing (provision) environment, purpose of processing, type of information, and others shall be considered comprehensively.
3. Adequacy Review & Additional Processing
Final evaluation as to whether pseudonymization was performed on a proper level to fulfill the purpose, and whether there is any risk of re-identification.
4. Follow-up management
Technical, managerial, and physical measures including compliance with laws must be taken for the pseudonymized information which has been evaluated as adequate.
Combination Procedure
Combining pseudonymized information
Legal basis
- Article 28-3 of the Personal Information Protection Act (Restriction on Combination of Pseudonymous Data)
- Article 29-2 of the Enforcement Decree of the Personal Information Protection Act (Combination of Pseudonymous Data among Personal Information Controllers)
- Notification on the combination and export of pseudonymized information
Combination procedure
 Enlarge image
Enlarge image
- Requesting Organization A
- Attributer
- Concatenated Key
- Serial No. A
- Requesting Organization B
- Serial No. B
- Attributer
- Concatenated key
- Transfer the concatenated key created through a method agreed upon by the management agency
- Concatenated Key Management Agency
- Transfer the linker information for the key
- Special Organization for Combination
- Combination
- (If requested)
- Review for Release
- Release if the result is satisfied
- Release