ISMS-P

The 'Personal information & Information Security Management System (ISMS-P)’ is an 'integrated certification system' that consolidated 'Personal Information Management System (PIMS) certification' and 'Information Security Management System (ISMS) certification' into one certification system, both of which were operated separately. ISMS-P has been enforced since November 7, 2018. Enterprises and institutions can expect to improve the external reliability of their personal information protection and security and reduce the risk of external and internal personal information infringements through the 'Personal information & Information Security Management System.'
Legal Ground
Article 32-2 of the Personal Information Protection Act (Certification of Personal Information Protection)
Procedure, certification system and criteria
Procedure
- Application for certification examination
- Certification examination
- Complementary measures
- Holding Certification Committee Meeting
- Issuance of certificate
- Follow-up management
Basic flow of the certification procedure
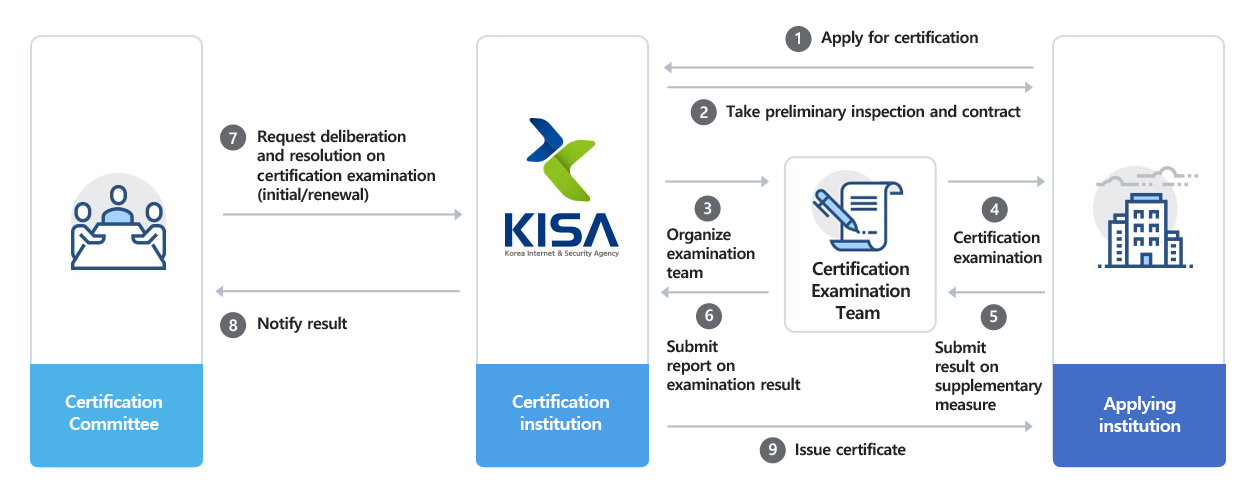 Enlarge image
Enlarge image
- Certification Committee
- Certification institution
- Requesting organization
- Application
- Preliminary exam and contract
- Organizing an examination team
- Certification examination
- Submitting the results of supplementary measure
- Submitting the report on the examination result
- Deliberation on the result & Request for resolution (new/renew)
- Notification of the resolution result
- Issuance of certificate
Certification system
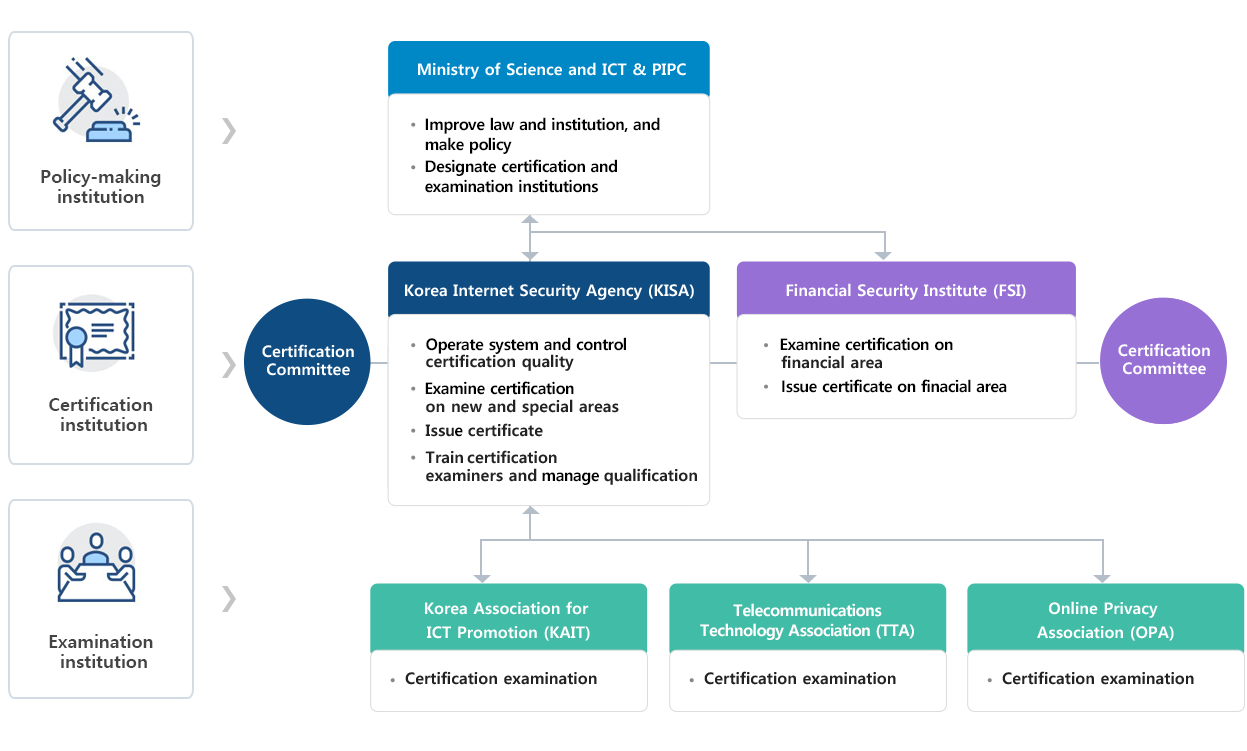 Enlarge image
Enlarge image
- Policy-making institution
- Ministry of Science and ICT & PIPC
- Improving law and policy, and policy making
- Designating certification and examination institutions
- Certification institution
- Certification Committee
- Korea Internet Security Agency (KISA)
- Operating the system and certification quality control
- Certification examination on new and special areas
- Issuing certificate
- Training the certification examiners and qualification control
- Financial Security Institute (FSI)
- Certification examination on financial area
- Issuing financial certificate
- Examination institution
- Korea Association for ICT Promotion (KAIT)
- Telecommunications Technology Association (TTA)
- Online Privacy Association (OPA)
- Certification examination
Criteria for Certification Examination
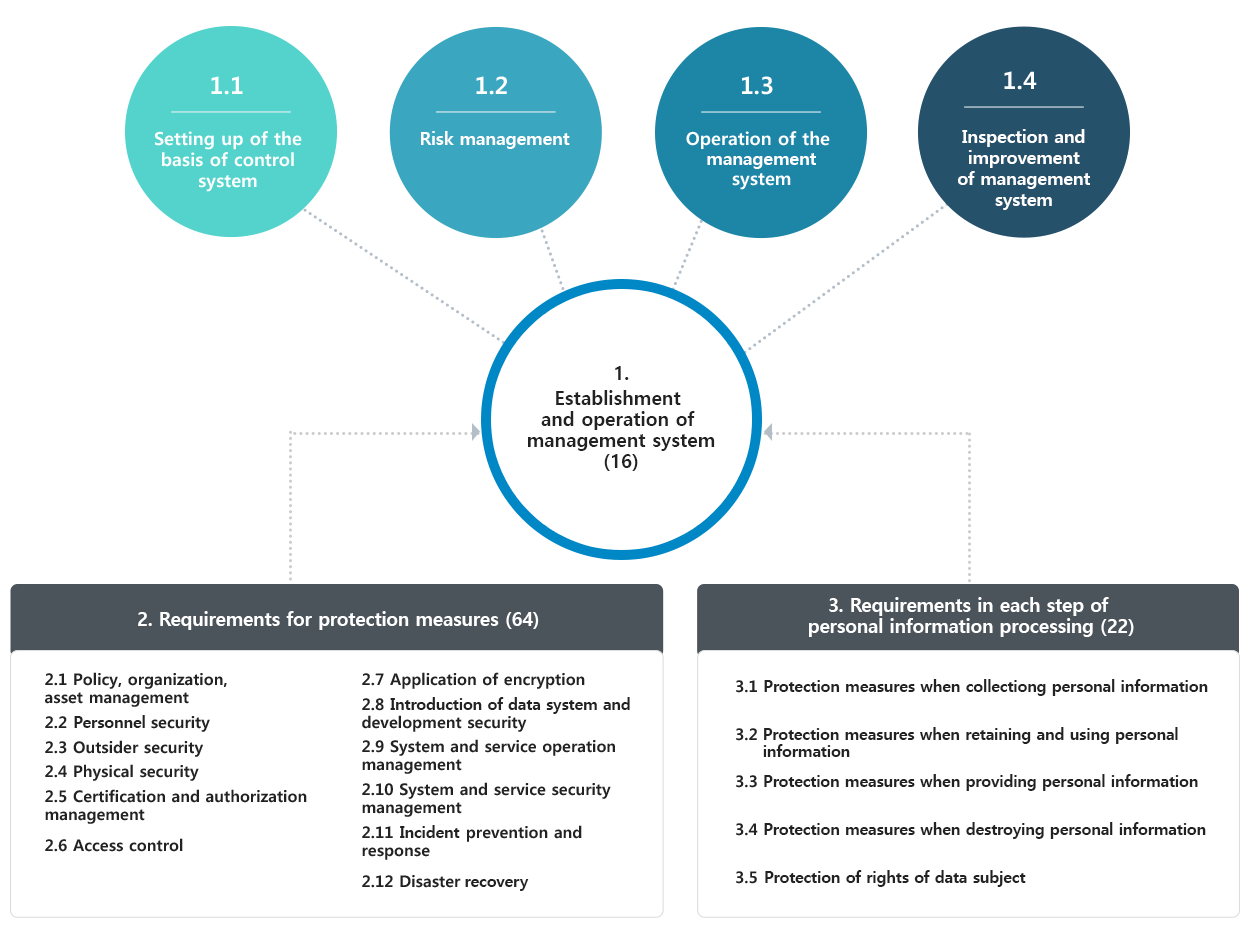 Enlarge image
Enlarge image
- Set-up and Operation of the Control System (16 items)
- Setting up of the basis of control system
- Risk control
- Operation of the control system
- Check-up and improvement of the control system
- Demands for Protection Measures (64 items)
- Policy, organization, asset management
- Personal security
- Outsider security
- Physical security
- Certification and authorization management
- Access control
- Application of encryption
- Data system introduction and development security
- System and service operation management
- System and service security management
- Accident prevention and response
- Disaster restoration
- Demands in Each Step of Personal Data Processing (22 items)
- Protection at the time of collecting personal data
- Protection when holding and using personal data
- Protection at the time of providing personal data
- Protection at the time of discarding personal data
- Protection of the rights of a data subject
| Classification | Integrated certification | Area (number of certification standards) | |
|---|---|---|---|
| ISMS-P | ISMS | 1. Establishing and operating management system (16) |
|
| 2. Requirements for protection measures (64) |
|
||
| - | 3. Requirements in each step of personal information processing (22) |
|
|